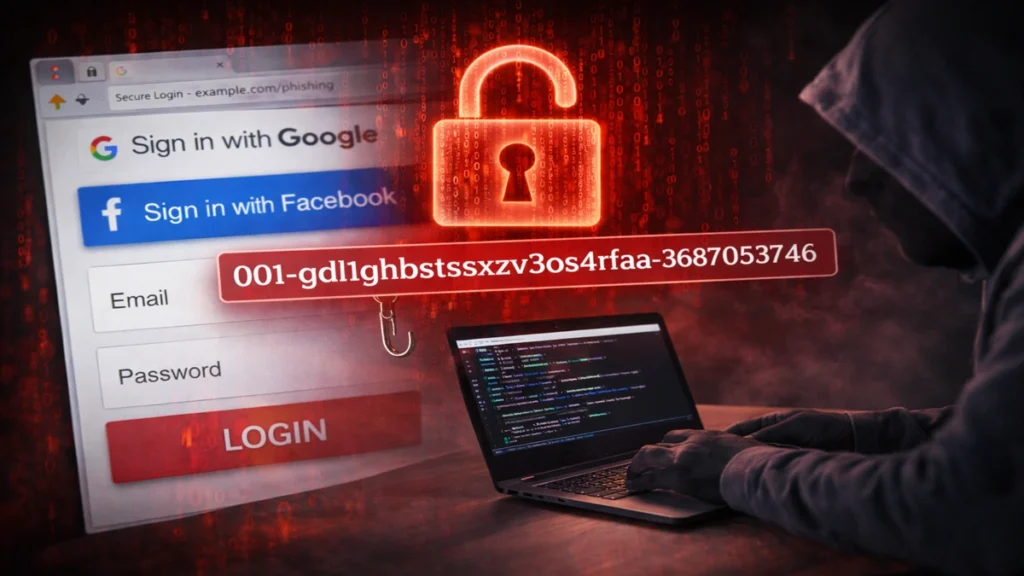
The string 001-gdl1ghbstssxzv3os4rfaa-3687053746 looks technical, precise, and purposeful. In reality, it is none of those things. It is a randomly generated alphanumeric identifier with no inherent semantic meaning, no dictionary definition, and no recognized technical standard attached to it. On its own, it is just data. What gives it importance is where it appears.
In recent phishing campaigns, strings like this have been embedded into URLs used in malicious redirection flows. They are used as tracking markers, session identifiers, or campaign tags by attackers who want to monitor which users click, which users submit credentials, and which attack vectors perform best. These identifiers allow criminals to run their operations with the same analytics discipline that legitimate marketers use.
The presence of this string in suspicious contexts is not a sign of a new technology or a hidden product. It is a sign of infrastructure. It points to a professionalized ecosystem of digital deception that targets specific user groups, especially professionals working in SEO, analytics, cloud platforms, and digital marketing.
Understanding this string therefore means understanding the systems that generate and deploy it. It means recognizing how attackers build phishing pipelines, how they abuse trust in major brands, and how small technical details can reveal large operational patterns.
This article explores how random identifiers function in phishing operations, why professionals are increasingly targeted, and how awareness of these mechanics can prevent compromise.
What the String Represents
Alphanumeric identifiers like 001-gdl1ghbstssxzv3os4rfaa-3687053746 are commonly used in software systems to track sessions, users, and events. They allow servers to distinguish one request from another and maintain continuity across complex systems.
In malicious campaigns, the same logic is applied offensively. Attackers generate unique identifiers for each victim or traffic source so they can:
• Track which ads or emails generate clicks
• Measure conversion rates for credential theft
• Separate high-value victims from low-value ones
• Adjust campaigns based on performance
The identifier becomes part of a telemetry system for criminal operations. It does not describe anything. It measures something.
This is why such strings appear in phishing URLs, especially those delivered through ads, redirects, or shortened links. They help attackers optimize their operations in real time.
The string itself is harmless. The system that deploys it is not.
How Brand Impersonation Campaigns Work
Modern phishing campaigns rarely resemble the crude scam emails of the past. They now mimic trusted brands, use paid advertising, and replicate legitimate interfaces with remarkable accuracy.
Attackers purchase search ads for keywords related to professional tools. When a user clicks the ad, they are redirected to a domain that visually resembles the real service but is controlled by the attacker. The page often disables normal login fields and forces users into social login options, particularly “Log in with Google.”
This is strategic. A single Google login can unlock email, analytics, advertising platforms, and cloud services simultaneously.
When a user enters credentials, the attacker captures them and either uses them immediately or sells them.
Tracking strings like 001-gdl1ghbstssxzv3os4rfaa-3687053746 allow attackers to understand exactly which ad, keyword, or region produced the credential.
Tokens in Legitimate and Malicious Contexts
| Context | Purpose | Risk |
|---|---|---|
| Session management | Maintain user state | Low |
| Analytics tracking | Measure engagement | Low |
| Ad redirection | Route traffic | Moderate |
| Phishing telemetry | Harvest credentials | High |
The same technical tools can be used for vastly different purposes depending on intent.
Why Professionals Are Targeted
Attackers increasingly target professionals because their accounts are more valuable. A compromised personal account may yield a few dollars. A compromised professional account can yield access to:
• Business analytics
• Advertising budgets
• Client data
• Domain ownership
• Email trust chains
This makes professionals attractive targets. Campaigns are therefore tailored to their workflows, terminology, and tools.
Attackers study professional behavior patterns and replicate them. They know which brands users trust, which interfaces feel familiar, and which workflows users follow automatically.
The more specialized the user, the more specialized the attack becomes.
Expert Perspectives
“Phishing has evolved into a performance-driven industry that mirrors legitimate digital marketing.”
“Social login is efficient for users and devastating when abused.”
“Tracking tokens in phishing URLs are evidence of operational maturity, not randomness.”
These perspectives reflect the shift from opportunistic scams to structured cybercrime.
Anatomy of a Phishing Pipeline
A typical pipeline follows these stages:
- Brand research and interface cloning
- Ad placement or email distribution
- Redirect through tokenized URLs
- Credential harvesting
- Account exploitation or resale
Each stage is monitored using identifiers like the string discussed here.
The sophistication of this pipeline means that technical awareness alone is insufficient. Behavioral awareness is equally important.
Risks of Credential Compromise
| Compromised Service | Impact |
|---|---|
| Impersonation and fraud | |
| Analytics | Data theft and manipulation |
| Advertising | Financial loss |
| Cloud services | Infrastructure compromise |
Credential theft is rarely isolated. It cascades.
Takeaways
• The string itself is meaningless but operationally important
• It functions as telemetry for phishing campaigns
• Professionals are targeted because their accounts are valuable
• Brand trust is the primary weapon used by attackers
• Awareness of structure is as important as awareness of content
Conclusion
001-gdl1ghbstssxzv3os4rfaa-3687053746 is not a word, a product, or a technology. It is a fingerprint of process. It is evidence of how modern cybercrime is built, measured, and optimized.
Understanding this helps shift thinking from “What does this mean?” to “Why is this here?” That shift is crucial. It moves users from curiosity to caution.
Phishing no longer relies on ignorance. It relies on automation, trust, and habit. The more those forces are understood, the less effective the attacks become.
Security today is not just about software. It is about perception.
FAQs
What is 001-gdl1ghbstssxzv3os4rfaa-3687053746
A random identifier used in redirect or tracking systems.
Is it dangerous
Not by itself, but its context may be.
Why is it used in phishing
To track victims and campaign performance.
Can it harm my system
No, but clicking associated links can.
How do I stay safe
Verify URLs, avoid ads for logins, and use strong authentication.